In this piece we will discuss:
- What are electronic and digital signatures?
- Objectives of the Digital Signature Methodology
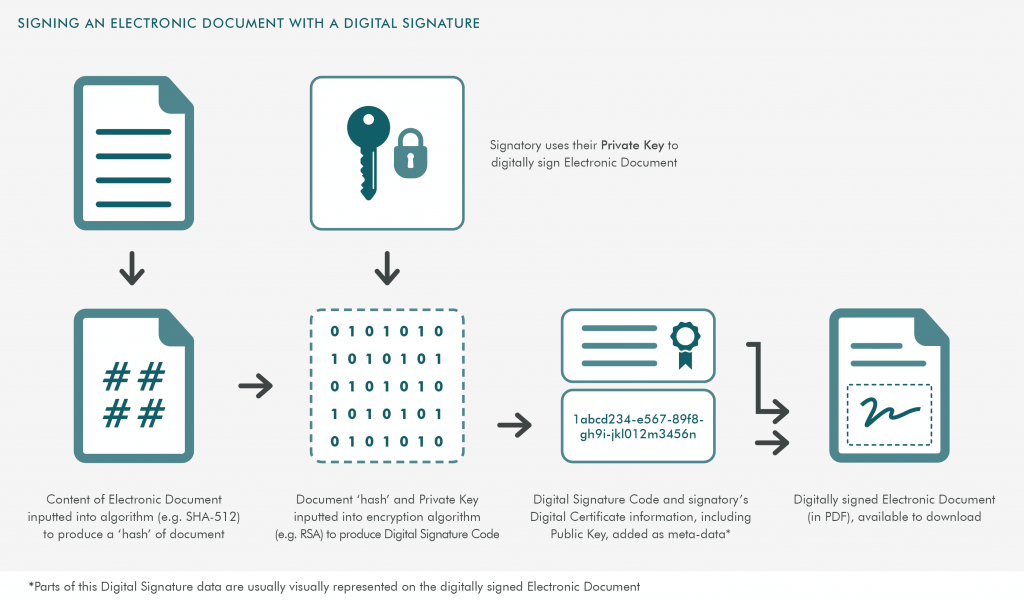
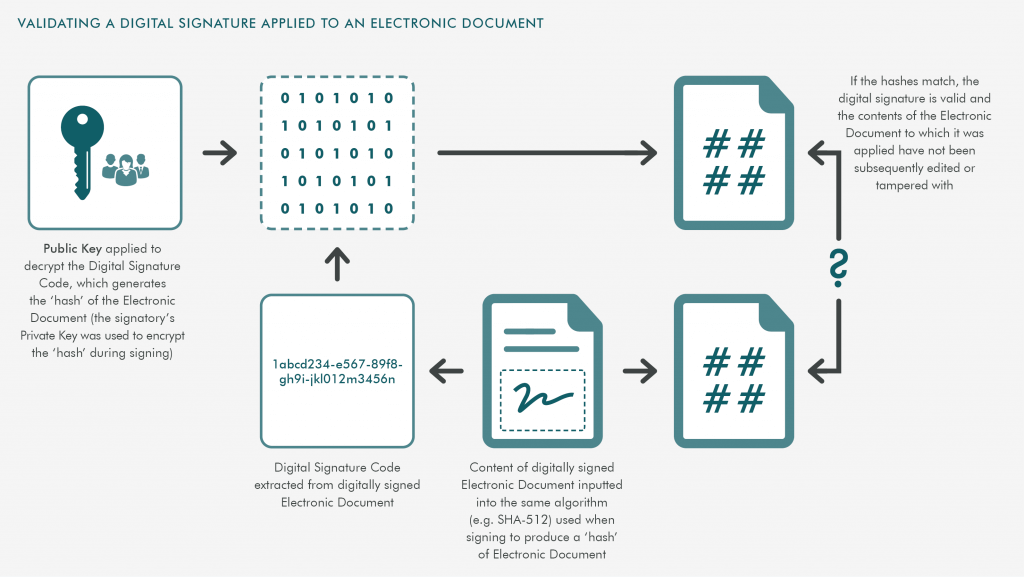
- Signing an electronic document with a digital signature
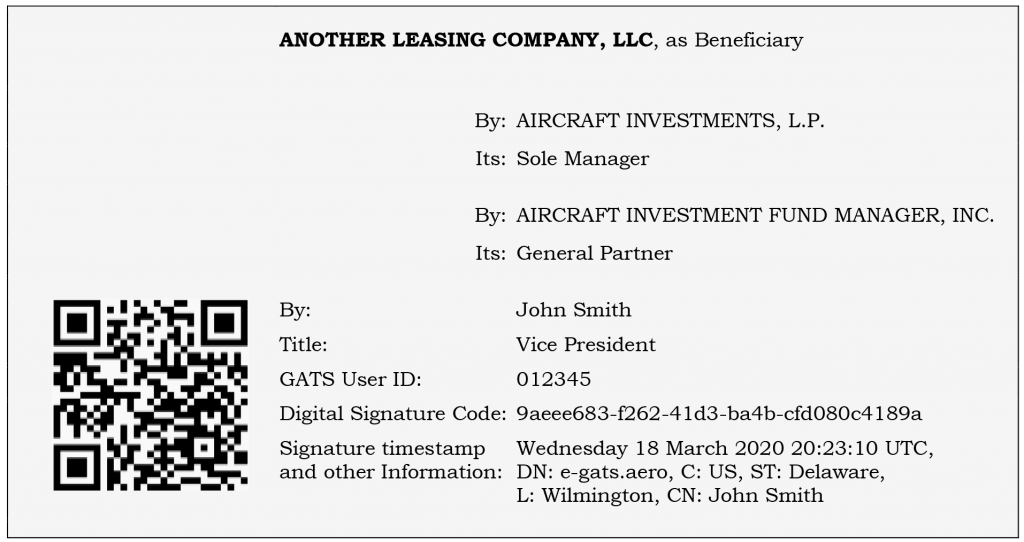
- Visual representation of digital signatures
- The GATS online platform: customisation; addressing logistical and practical challenges